CVE-2024-31735: LibEvent Library Memory Leak
Leviathan Security Group has discovered an issue with LibEvent and is publishing this disclosure on 05/14/2024. CVE-2024-31735 has been assigned to this issue.
Have questions about this disclosure? Reach out to us here.
Executive Summary
Our research group found a memory leak in the LibEvent Library v2.1.12-stable that allows an attacker to cause a denial of service (DoS) via the evbuffer_add_file function. The corresponding CWE is CWE-401: Missing Release of Memory after Effective Lifetime.
Technical Details
A memory leak occurs when a program fails to free memory that it no longer needs, resulting in a gradual accumulation of unused memory over time.
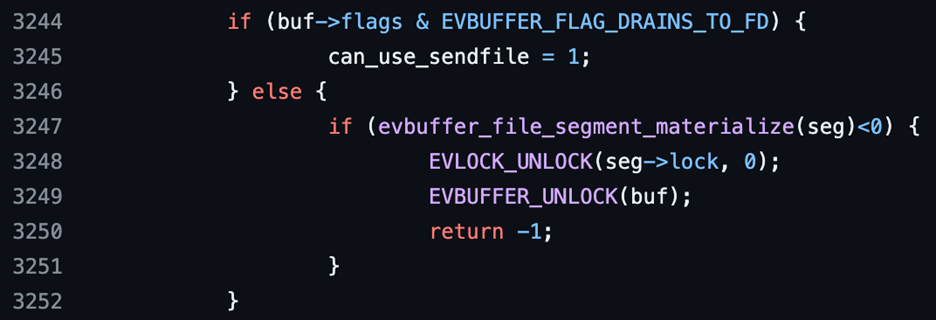
In the library, we identified a memory management vulnerability in an evbuffer_add_file function. This function is responsible for copying data from a file into an evbuffer that is used to write to a socket. The evbuffer_add_file function is critical for the management of data transfer. We discovered an error-handling oversight within this function. Specifically, if the internal evbuffer_add_file_segment function encounters an empty file during the data transfer process, it returns -1 without freeing the associated evbuffer_file_segment structure:
This oversight results in a memory leak because the memory allocated for the structure remains in use even though the function has exited with an error.
Attacker Value
This memory leak vulnerability in a critical library is a significant problem for any software that uses it. Attackers could exploit this vulnerability to disrupt services, compromise system stability, or gain unauthorized access to sensitive data within applications that rely on the library.
In a real-world scenario, an attacker could exploit the memory leak vulnerability in the library by flooding the server with a large number of empty files. Each file triggers the memory leak in the library, gradually consuming system resources and causing memory exhaustion. As the server becomes overwhelmed with processing these files and managing the leaked memory, its performance degrades, eventually leading to service unavailability or crashes.
Credit
This issue is being disclosed through MITRE’s CNA and is credited to Viktoriia Reitsenshtein, a Senior Security Consultant at Leviathan Security Group.
Timeline
2024-02-12: Initial findings presented to LibEvent maintainer.
2024-02-19: PoC validated by package maintainer.
2024-03-03: Package maintainer applied bugfix to repository and pushed the commit to the main branch.
2024-04-01: MITRE contacted for CVE ID reservation.
2024-04-11: MITRE responded with CVE ID CVE-2024-31735 for the reported vulnerability.
2024-06-06: Public disclosure of CVE-2024-31735.